It's that scary moment... You're getting some work done on your computer when you see a dreaded pop-up message:
CryptoLocker, CryptoWall and other crypto-/ransom-ware has been in the news again (or still?). This kind of malware attack was first identified in 2013. Rather than trying to steal information, the malware encrypts your files. But you don't have the key to decrypt. The attacker offers, through a pop-up message, to "sell" you the "service" to unlock your files. To make things worse, the attacker threatens to delete the keys after a set amount of time, typically 72 hours, which could prevent you from recovering the files.
These ransom-ware viruses are usually sent to your computer as an email attachment. The attachment can be an office file, pdf, zip file or other file. The malware can also come from an infected web link.
When your computer is infected, the virus operates quietly in the background, encrypting files. You usually won't know there's a problem until the files are encrypted, and then you're in trouble.
So if you are infected and encrypted... then what? Well, there's bad news, good news, more bad news and some more potentially good news!
A place to talk about information security, Internet safety and, of course... coffee!
Thoughtful, sometimes controversial, but not following the crowd unless I'm in line at the coffee shop.
Tuesday, August 18, 2015
Crypto Where?
Labels:
advanced,
anti-malware,
anti-virus,
attachments,
attack,
computer,
consumer,
crypto,
cryptowall,
cryptoware,
email,
encryption,
exploit,
key,
malware,
phishing,
ransom,
ransonware,
virus
Tuesday, August 4, 2015
See the Man With the StageFright
I always liked the way Rick Danko sang that song, and I saw him perform it a few times.
 But now we have a new StageFright, a vulnerability in the base android phone operating system. This is an equal-opportunity vulnerability effecting all android phones (nearly 1 billion!). Like many new vulnerabilities discovered in the past year, this one has a name and a logo.
But now we have a new StageFright, a vulnerability in the base android phone operating system. This is an equal-opportunity vulnerability effecting all android phones (nearly 1 billion!). Like many new vulnerabilities discovered in the past year, this one has a name and a logo.
The issue is a "feature" in the way androids pre-processes MMS multi-media messages (pictures, videos) sent via your text messaging app. That could be the stock messaging app, a custom messaging app from your phone manufacturer or data provider, or even Google Hangouts.
Here's why the vulnerability is so bad... you don't have to open the message! You don't even have to know that you received the message. All it takes is for your phone to automatically download a malicious message in the background - which is exactly what it does - for your phone to be owned! That's a problem.
At the time I wrote this column, there seems to be a fix only for Google-branded phones, and that's a very small percentage of all phones. You can check with your carrier to find out when you'll get a patch.
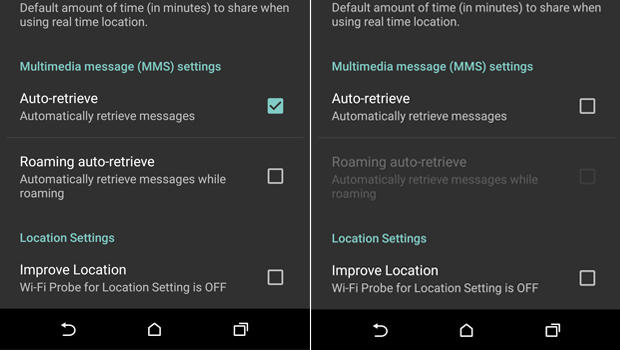
Meanwhile, there is a work-around. You need to configure your messaging app to not automatically download MMS messages.
 But now we have a new StageFright, a vulnerability in the base android phone operating system. This is an equal-opportunity vulnerability effecting all android phones (nearly 1 billion!). Like many new vulnerabilities discovered in the past year, this one has a name and a logo.
But now we have a new StageFright, a vulnerability in the base android phone operating system. This is an equal-opportunity vulnerability effecting all android phones (nearly 1 billion!). Like many new vulnerabilities discovered in the past year, this one has a name and a logo.The issue is a "feature" in the way androids pre-processes MMS multi-media messages (pictures, videos) sent via your text messaging app. That could be the stock messaging app, a custom messaging app from your phone manufacturer or data provider, or even Google Hangouts.
Here's why the vulnerability is so bad... you don't have to open the message! You don't even have to know that you received the message. All it takes is for your phone to automatically download a malicious message in the background - which is exactly what it does - for your phone to be owned! That's a problem.
At the time I wrote this column, there seems to be a fix only for Google-branded phones, and that's a very small percentage of all phones. You can check with your carrier to find out when you'll get a patch.
Meanwhile, there is a work-around. You need to configure your messaging app to not automatically download MMS messages.
- Open you rmessaging app.
- Go to Settings
- Select: Multimedia messages
- un-select Auto Retrieve
Now, when someone tries to send you a message with multi-media content, you'll see that the message arrived, but the photo or video will not be downloaded. Only tap to download if the message came from a trusted source.
Of course, you should also keep your phone patched by applying all phone and app updates. And... get rid of any apps you don't need.
Here are some references for more info.
Subscribe to:
Posts (Atom)